Today is a short post in which we will demonstrate a very simple example of using REnigma to scrape memory from a recording. We are currently developing new memory analysis capabilities with REnigma including the ability to use GDB to interact with a running replay, so this post will illustrate some of what is coming up for REnigma users in the near future.
First, we were on Hacker News earlier today and noticed this challenge...
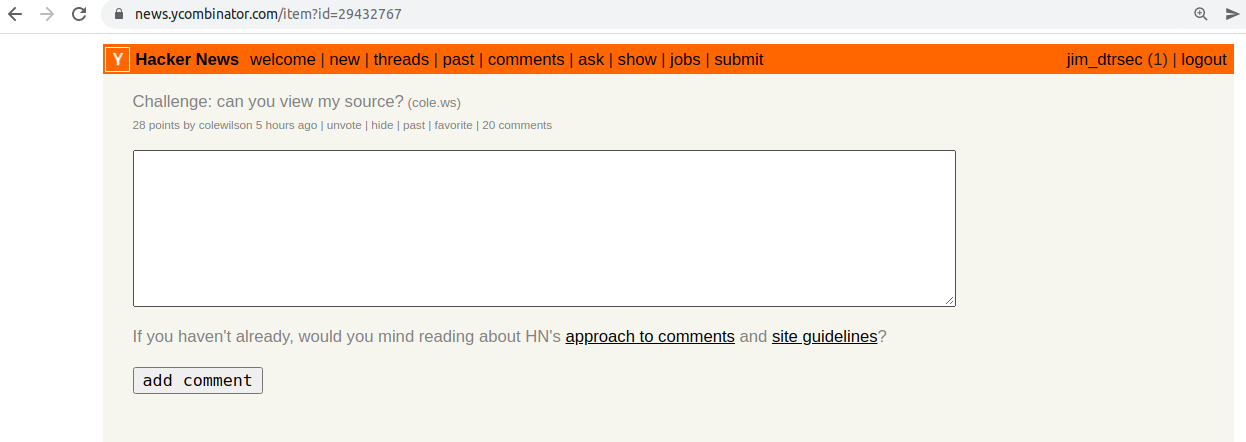
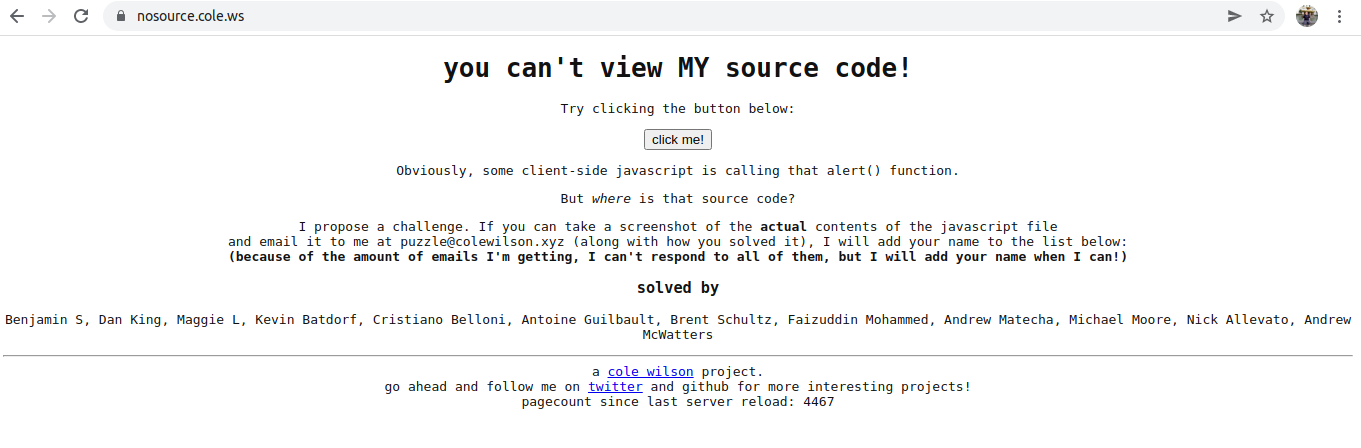
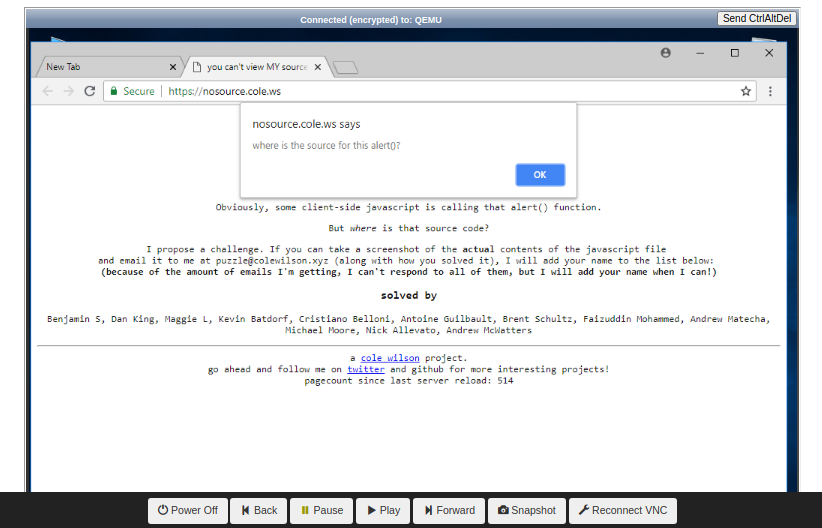
This piqued our interest, so we did what everyone does first and viewed the source...
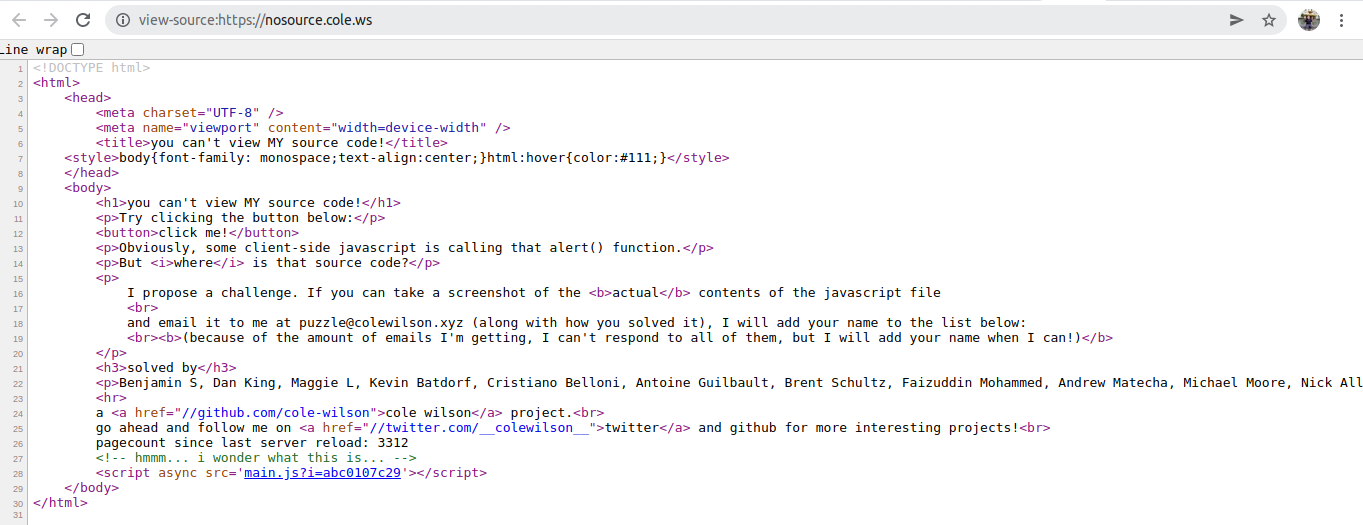
There's a javascript file referenced in there, so we tried to go check that out and got this taunt...
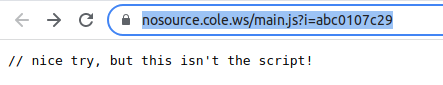
Like Michael Jordan, we took that personally. It was time to use REnigma.

We went to the website in the VM and clicked on the button to make the alert show up. Then we ran a replay and found an execution point where the Javascript alert was on the screen.
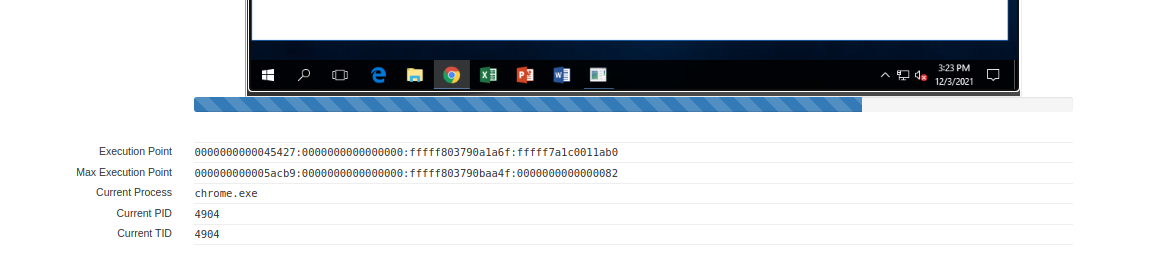
Scrolling down on the REnigma web interface, we can see the execution point is...
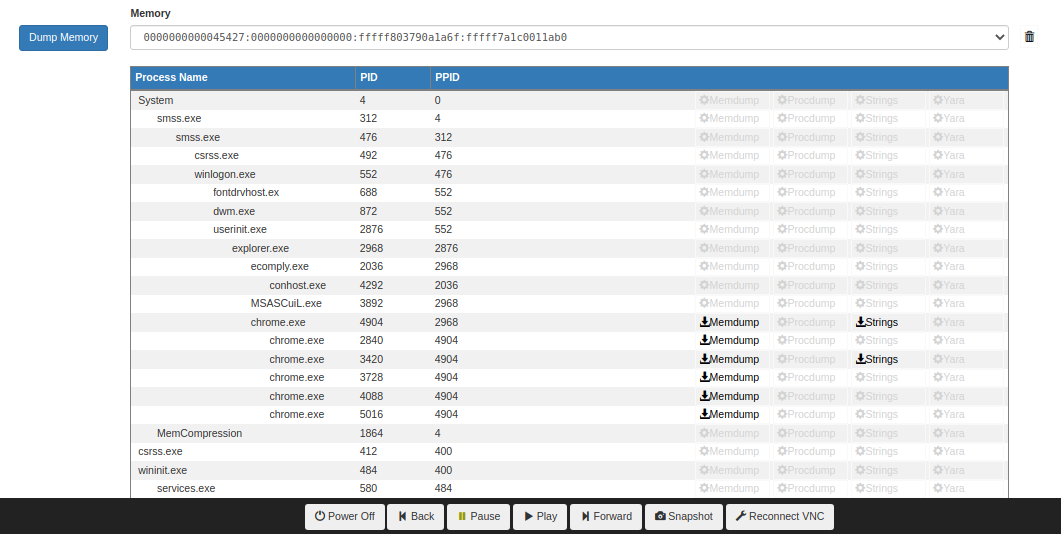
Then we took a memory dump at that execution point and ran the "Pstree" analysis on the memory dump. Then in the Pstree view, we dumped the strings for the main chrome.exe process (pid 4904) that is the parent of the other chrome.exe processes. In Chrome, this parent process acts as a sandbox for the child rendering processes and handles all system interactions for the children.
We then looked at the strings dump from pid 4904. We found the string "where is the source" in memory several times. The strings analysis from REnigma also gives us the virtual address of the string. In this case, the string is located at virtual address 0x25ca4b13387 in pid 4904.
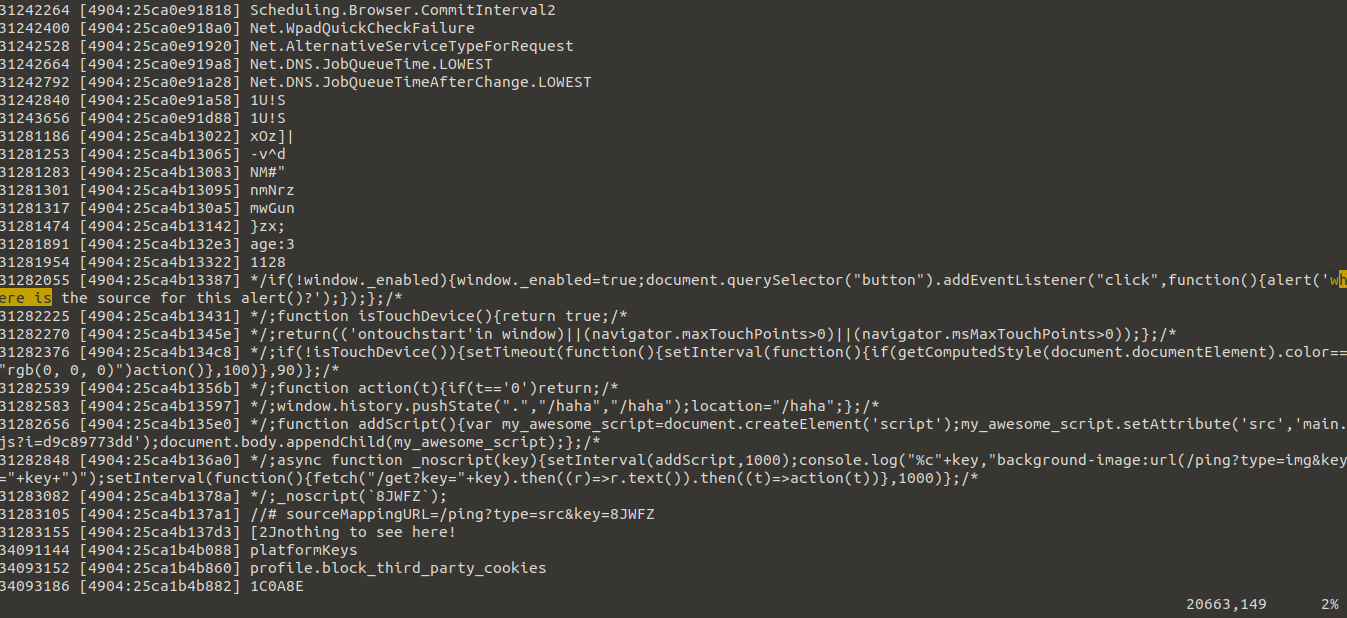
Then, just for fun, we used REnigma's new regdb tool to set up a GDB stub server for the running VM at the execution point of interest. We were then able to do a remote gdb debugging session to see the strings directly in the memory of the paused replay VM.
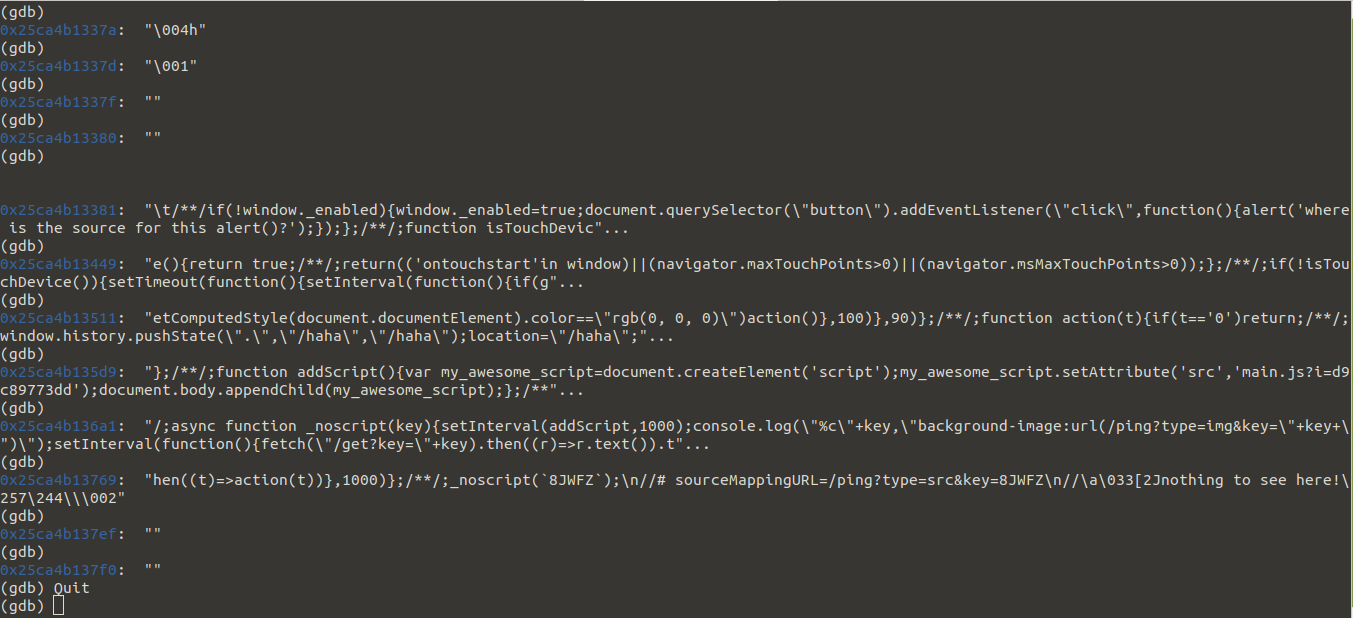
While the author of this website probably used every Javascript trick in the book to try to make viewing the source hard (just as a malware author would like to do), this was a piece of cake for REnigma since there is nowhere to hide when you can just introspect the memory at any point during a recording.