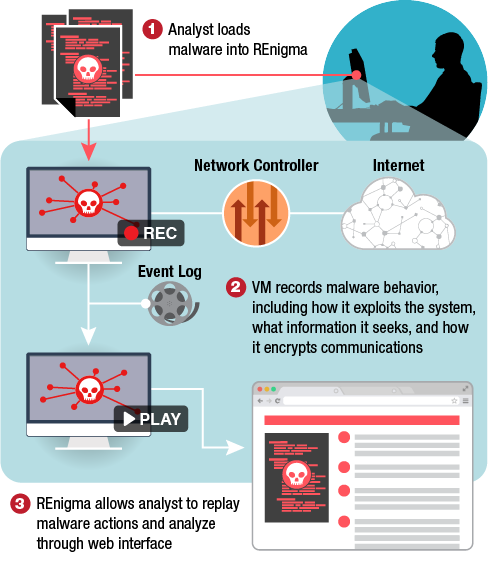
The key innovation that powers REnigma is a technology called Record and Replay. The essence of Record and Replay is to perfectly capture every state change that occurs in a virtual machine with extreme efficiency, during the recording phase, so that it can be replayed and analyzed offline. Record and Replay is unique to REnigma and took more than 5 years of research at The Johns Hopkins University Applied Physics Laboratory to create (see about page for history of REnigma). REnigma builds on top of Record and Replay as depicted in the figure. First, the user loads a suspicious URL or file into REnigma (1). Next, the user starts an interactive recording and detonates the suspicious sample in a throw-away virtual machine at speed, perfectly capturing all activity (2). After completing the capture phase, the user can pull out artifacts, second stage samples, and even replay the execution instruction-by-instruction or create memory dumps at previous points to pick apart the sample (3).